Introduction
Maintaining secure and reliable access to EC2 instances is important for any AWS infrastructure. However, there are times when due to unforeseen circumstances access is lost due to misconfigurations, network issues, or a security breach. In such cases, where the access is lost, we can regain access using AWS Systems Manager (SSM), which allows users to connect and run commands on an EC2 without the need for direct SSH or RDP connections. In this blog post, we will explore how to recover access to an EC2 instance using SSM, providing the steps and listing the importance of proactive measures to prevent such situations.
Pre-requisites
Ensure that the SSM agent is installed and running on the EC2 instance, as it facilitates communication with the Systems Manager service. SSM Agent is installed, by default, on Ubuntu Server 22.04 LTS, 20.04, 18.04, and 16.04 LTS 64-bit AMIs with an identifier of 20180627 or later.
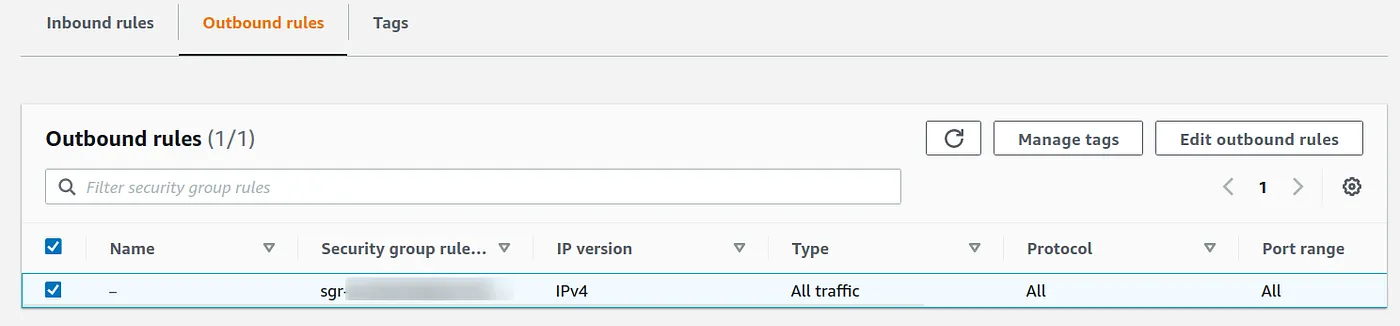
To connect with the EC2 instance it also requires outbound rules to have 0.0.0.0/0 on all TCP ports
How to Recover Access
There are two ways to connect using SSM one is from the EC2 Instance dashboard directly and the other is from AWS Systems Manager. The steps for both ways are mentioned below
- Ensure EC2 Instance Configuration for SSM:
Before attempting to recover access using SSM, confirm that the EC2 instance is properly configured: Verify that the instance has an IAM role attached, granting it the necessary permissions to communicate with SSM.
a. Ensure the AmazonSSMManagedInstanceCore policy is attached to the EC2 instance role
b. Ensure that AWS Organisations isn’t blocking any of the services that are required. Key services you need to allow in organizations are
ec2:* ec2messages:* ssm:* ssmmessages:* s3:*
c. Once all the requirements are fulfilled. Select the Instance and click on Connect. Once the Connect to Instance page opens under the Session Manager click on Connect.
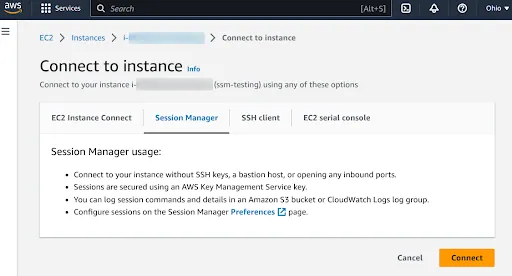
The SSM session will start and you will have access to the EC2 instance via the interactive shell.
- We can also connect to EC2 instance using AWS Systems Manager Console. Below are the steps
- In the AWS Systems Manager console, under Node Management select Session Manager. Once the Session Manager screen opens click on Start session
- Under Specify target select the specific EC2 instance you wish to recover access.
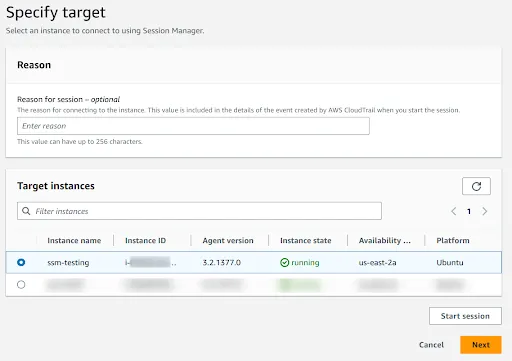
- On the EC2 instance details page, click on the “Start Session” button. This action will initiate an interactive shell session within the Systems Manager console, establishing a secure channel to execute commands on the EC2 instance.
- The next step is to mention a custom document to configure session settings, including duration, encryption, and logging. It is optional and go to the next page.
- On the Review and Launch page click on Start Session

- Once the SSM session starts, you will have access to the EC2 instance via the interactive shell.
- Diagnose and troubleshoot any issues that might have caused the access loss, such as firewall misconfigurations, SSH key problems, or user account issues.
- Rectify the identified issues and restore access to the EC2 instance.
Taking Proactive Measures
To prevent access issues in the future, consider implementing the following best practices:
- Review and update IAM roles and permissions to ensure the appropriate level of access for EC2 instances.
- Update the SSM agent on EC2 instances to benefit from new features and security enhancements.
- Implement strict security measures, such as regularly rotating SSH keys, enforcing strong password policies, and utilizing multi-factor authentication (MFA) where applicable.
- Audit and monitor EC2 instances for any suspicious activities or unauthorized access attempts.
- Implement network security groups and firewalls to restrict access to EC2 instances based on the principle of least privilege.
- By following these measures, you can significantly reduce the risk of losing access to EC2 instances and maintain a secure and robust infrastructure on AWS.
Conclusion
AWS Systems Manager offers a reliable and secure method for recovering access to EC2 instances through its SSM service. By leveraging SSM, you can regain control over instances without exposing them to external connections or requiring direct SSH or RDP access. This not only enhances security but also streamlines access management and troubleshooting processes. However, it is essential to establish proactive measures to prevent access loss, such as regularly reviewing IAM roles, keeping the SSM agent up to date, and implementing robust security practices.
